Introduction
A little more than a decade ago when the term Cloud, Cloud computing, and other terms associated with enterprise IT systems started to become part of technical discussions and mainstream IT topics, most IT professionals and managers, let aside outsiders, acted more in disbelief than with optimism. The initial reactions to Cloud computing and what it represented were mostly hostile. Instead of seeing Cloud computing for what it was and what it could become in the future, most IT managers were busy finding issues and raising concerns, mostly out of their self-induced paranoia of letting go of their little control areas. Most IT professionals viewed Cloud computing as a threat, something which would, if implemented, take away their most important assets – physical computing resources and put those in hands of an outside organization.
Fast forward 10 years, there has been a remarkable adaption of Cloud Computing services and its various sub-sections across IT industry. This remarkable adaption and emergence of market leaders AWS and Azure has fed a potential frenzy of activity around Cloud computing. The initial feelings that ranged from outright debunking Cloud’s potential at worst to careful cautious optimism at best have been left behind in dust long back. More than a decade or so later, Cloud computing has come a long way.
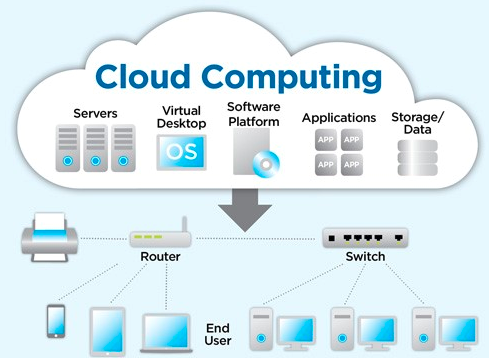
Image Source: World Informatix Cyber Security
Need for Security
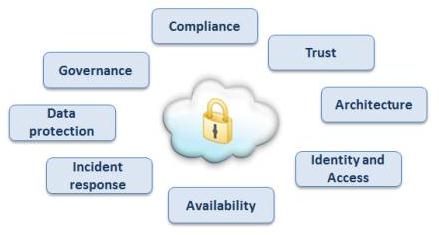
The clouds surrounding Cloud Computing were as ominous then as they remain today, at least from security point of view. Many debated if it was possible that someone outside the organization be responsible to manage the IT infrastructure’s needs that the organization runs on? Could someone outside the organization be responsible to setup, operationalize, manage and provide security for organization’s IT and digital assets stored using IT infrastructure? The first and foremost concern expressed was around the security. As with any maturity model, the debate picked up and became a part of mainstream discussions as the industry moved towards gradual and in some cases scaled adoption of Cloud. More than a decade later, the debate is still raging. Security remains the primary concern, though the ecosystem itself has grown leaps and bounds and shifted in direction far, far away from the humble beginnings. In many ways, it is fair to say that while the ecosystem has completely transformed to the point that it bears little resemblance to what it was 10 years ago, the debate on Security has retained its position at the top of the concerns expressed by IT managers.

Image Source: Stratosphere Networks
Most organizations, IT included, recognize data as the most powerful resource today. Due to interconnected everything, every single swipe of finger or each step during the morning walks, or what one buys, how much, from where, at what price and at what time of day, every single aspect of life is being recorded and getting stored somewhere in deeper and deeper oceans of information. This massive amounts of data generated everyday by the myriad of systems in turn is being used to start controlling human decisions at first, providing intelligence and inputs to assist in human decision making process with the stated or unstated aim of taking over the decision-making process completely. Other than that, possession of the data has more immediate, financial and tangible benefits associated with it.

Image Source: IBM
The value of data has given rise to a host of platforms, systems, rules and standards aimed at keeping this treasure trove of information secure from falling in to wrong hands. With high-profile data breaches continuing to occur with alarming regularity across industries, IT security professionals are revamping their strategies to stay a step ahead. In fact, the security environment has become increasingly hostile, and the threat models so varied, that few in-house IT teams have the resources or bandwidth to keep ahead of the curve and protect their data systems.
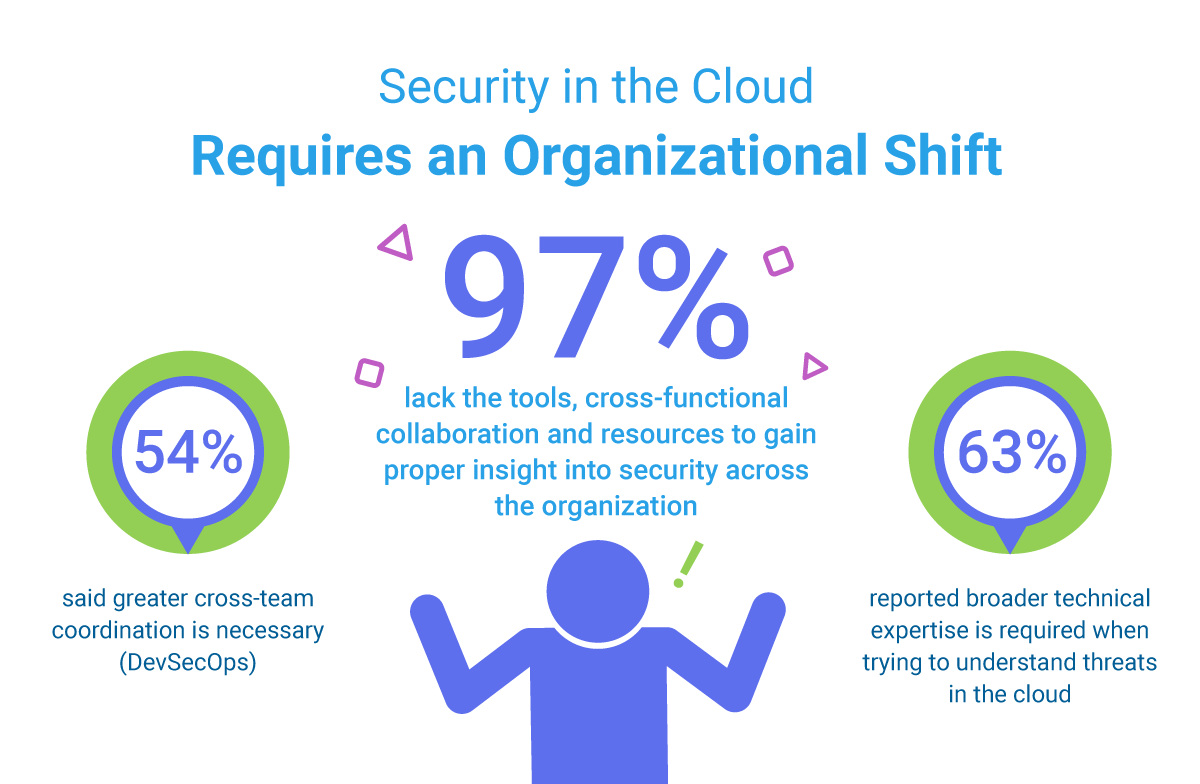
Image Source: Sumologic
Security in Cloud
The security apparatus applied includes physical infrastructure like secure siting, resilience against natural disasters, and other specialized hardware; software and applications such as network stacks, applications exposed to internet, etc; logical assets like processes and policies, disaster recovery plans, etc; and non-tangibles like skills and experience of security professionals. Every single layer of the stack is a potential vulnerability, and responsibility of IT to secure it. A weakness at any point means that someone can gain a foothold into IT infrastructure and use that leverage to move around, find further vulnerabilities, and inflict damage.
Image Source: DataFlair
The attackers with malicious intent are getting savvier by the day. Any new advancements in security technologies is met or at times even exceeded by counter-measures from perpetrators of attacks on IT systems. This means that security measures and features must be constantly revamped and upgraded. Today, only the world’s most sophisticated businesses can deploy the technology and staff needed to counter today’s threat environment. And the deeper a company’s footprint across the technology stack, the more complex (and resource-intensive) this effort becomes.
In the case of a recent, well-known breach at Target, perpetrators got in due to low security measures implemented on the systems embedded in the air conditioning control systems and used that access to penetrate more valuable, vulnerable systems on the network.
The many advantages of adapting and using Cloud as the primary answer to meet IT needs have been discussed widely. These range from financial benefits – lowering cost of ownership and maintenance, shifting infrastructure costs from capital to operating on balance sheet, lowering upfront expenditure, and better ROI moneys invested. These financial benefits provide much needed business flexibility that comes with Cloud computing. More benefits, perhaps equally significant, range from quicker response times, to elasticity, and to scalability that are intrinsic to on-demand computing resources. Finally, a significant benefit not often discussed in business case studies is that cloud infrastructure also delivers a much resilient and stronger security stack.

Image Source: DZone
The wide range of services offered by cloud computing companies can be categorized into three basic types:
- Infrastructure as a Service (IaaS). IaaS provides users access to raw computing resources such processing power, data storage capacity, and networking, in the context of a secure data center.
- Platform as a Service (PaaS). Geared toward software development teams, PaaS offerings provide computing and storage infrastructure and also a development platform layer, with components such as web servers, database management systems, and software development kits (SDKs) for various programming languages.
- Software as a Service (SaaS). SaaS providers offer application-level services tailored to a wide variety of business needs, such as customer relationship management (CRM), marketing automation, or business analytics.
Cloud infrastructure employs a critical approach better known as “Security by design”. This approach is intrinsic to modern cloud architectures. The logical controls and policy based separation among infrastructural components ensure a level of compartmentalization and segregation that few traditional data center platforms can offer. This segregation keeps compartments secure and agnostic to each other in the event of threats and potential attacks. Thus, organizations employing cloud computing begin with a much higher security standard and employ that standard as a baseline and not an aspirational level, across the entire perimeter.
Perhaps most importantly, as cloud computing platforms are marketed and run as services, not just code, operational security — whether it’s resilience against DDoS (distributed denial of service) attacks, proactive detection of malicious code, or ensuring the integrity of messages in transit — has become a fundamental quality of any cloud computing business. Security is paramount and it has never been more in focus. This requirement of providing higher levels of security alone enables the information security teams to move away from a primarily reactive (and losing) position of plugging the holes towards assuming a proactive, aggressive stance that’s fundamental to an organization’s overall IT strength and technology expertise.
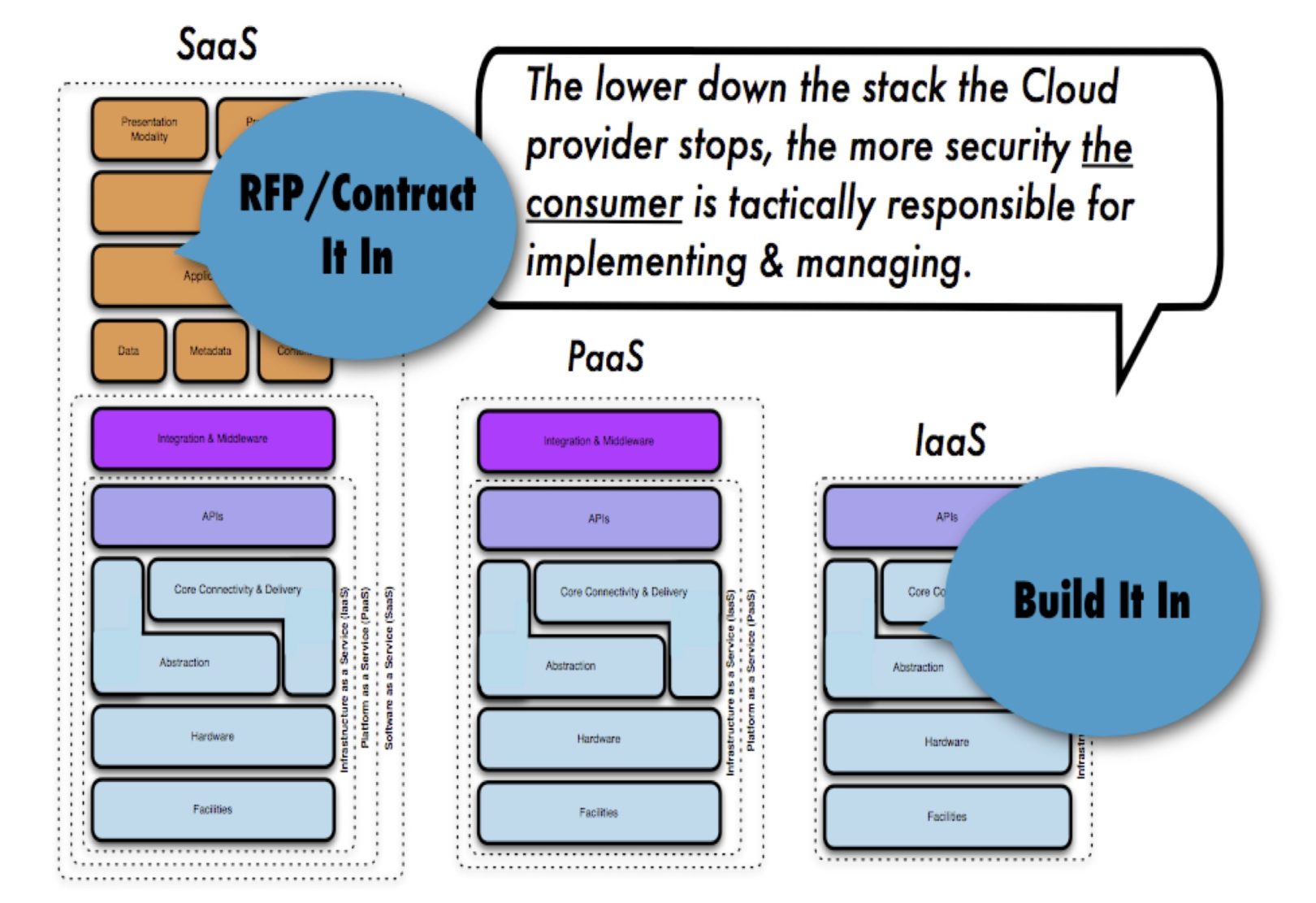
Image Source: SDxCentral
The focus and shift towards security, making security the prime area of strength which defines almost all other parts of IT strategy alone represents a major shift in the quality of security of technology services. And, as cloud infrastructure providers now have the scale and importance to attract the best security and reliability engineering professionals in the world, the standards are continuously being refined, getting better with each iteration and with each attack. But there’s another factor at work, as well.
Security in Cloud – A shared Responsibility Model
The way cloud security is delivered largely depends on the individual cloud provider or the cloud security solutions enterprise has chosen. However, implementation of cloud security processes is always a joint responsibility between the business owner and solution provider.
Cloud service providers treat cloud security risks as a shared responsibility. In this model, the cloud service provider covers security of the cloud itself, and the customer covers security of what they put in it. In every cloud service—from software-as-a-service (SaaS) like Microsoft Office 365 to infrastructure-as-a-service (IaaS) like Amazon Web Services (AWS)—the cloud computing customer is always responsible for protecting their data from security threats and controlling access to it.
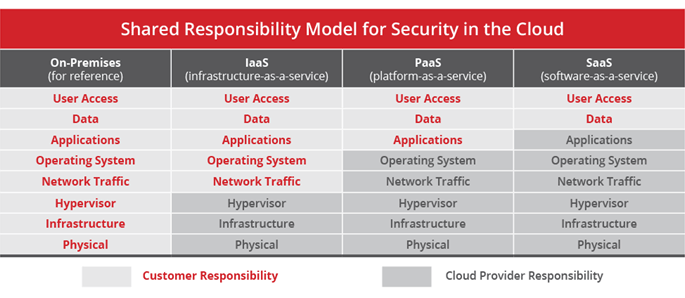
Image Source: McAfee
Conclusion
Its not difficult, nor it is far-fetched idea to imagine that Cloud is the way of the future. In fact, cloud is the future of IT. Cloud has already become a part of most enterprise’s tactical and strategic IT plans, while others are getting there in their adaption of Cloud. It’s not a far-fetched technical story any more requiring the attention of only IT department, it’s at the center stage of revamping each organization’s arrangement of IT infrastructure and the way IT is run and managed. Security has remained and is still the most basic yet the most important challenge, and the entire industry.

Image Source: PRNews
Today, most organizations view cloud-based services as a better way to deliver the services they need, including data protection and security. The risks and costs associated with maintaining self-managed, in-house IT security teams who manage organization’s IT infrastructure as a strategic answer to address security concerns is prohibitively high. Add to it the need to constantly upgrade skills and knowledge levels to respond to ever changing security landscape, changing and ever deepening nature of attacks, and redundancy of IT equipment at a faster pace than before, make it a luxury that many cannot afford. That’s precisely why most IT teams today understand that self-managed infrastructure — whether in-house or in third-party data centers — is almost always more tedious, less secure and more expensive than more modern, cloud-based alternatives.